Sup guys,
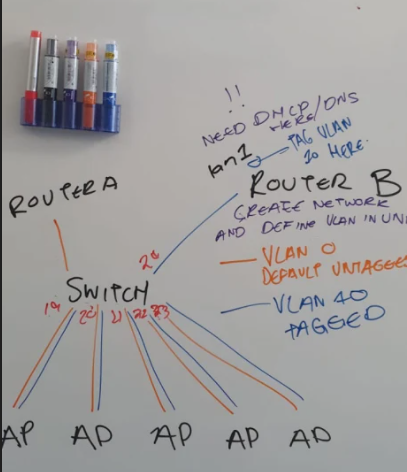
Got a question that's giving me trouble trying to configure something, please bear with me, always built hardwire LAN's, the need came up for a VLAN now and it's actually my first time setting up VLAN's where 2 networks need access to the same port.
HP Switches, 1920s's. VLAN options are include/exclude, Tagged/untagged.
I have 6 ports that needs access to two different networks, 5 of them will power AP's with 2 SSID's each, one for the secondary network VLAN attached to the Gateway.
My understanding is that it should be simple to set up, tag both Native VLAN and secondary VLAN to the first 5 ports, tag only port 6 to secondary VLAN for internet access, then leave all other ports untagged on both VLANs.
Doing that throws the AP's off the native VLAN. Since network 1 remains the native VLAN, I'm quite sure the AP's should remain online there correct? Also, the Include/Exclude options seems to confuse this all more. Leaving ports untagged should keep them invisible to the other VLAN, so what's the include/exclude options there for? Or am I missing something?
Thanx upfront!
Got a question that's giving me trouble trying to configure something, please bear with me, always built hardwire LAN's, the need came up for a VLAN now and it's actually my first time setting up VLAN's where 2 networks need access to the same port.
HP Switches, 1920s's. VLAN options are include/exclude, Tagged/untagged.
I have 6 ports that needs access to two different networks, 5 of them will power AP's with 2 SSID's each, one for the secondary network VLAN attached to the Gateway.
My understanding is that it should be simple to set up, tag both Native VLAN and secondary VLAN to the first 5 ports, tag only port 6 to secondary VLAN for internet access, then leave all other ports untagged on both VLANs.
Doing that throws the AP's off the native VLAN. Since network 1 remains the native VLAN, I'm quite sure the AP's should remain online there correct? Also, the Include/Exclude options seems to confuse this all more. Leaving ports untagged should keep them invisible to the other VLAN, so what's the include/exclude options there for? Or am I missing something?
Thanx upfront!